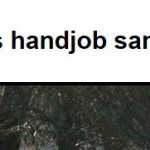
 I’ve had a problem over the past few months with someone hacking these Project Notes. The symptom is a link with text “handjob santa” added very intermittently to the title block of the pages. It has appeared immediately after “Jim’s Projects” and after “Workshop 88”. The link points to a non-existent or expired domain (opengadgets.net/handjob-santa). Thankfully, the hack isn’t very harmful.
I’ve had a problem over the past few months with someone hacking these Project Notes. The symptom is a link with text “handjob santa” added very intermittently to the title block of the pages. It has appeared immediately after “Jim’s Projects” and after “Workshop 88”. The link points to a non-existent or expired domain (opengadgets.net/handjob-santa). Thankfully, the hack isn’t very harmful.
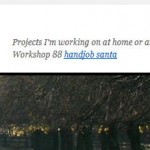 I first saw it very briefly (and then not there – triggering the usual “Did I really see that!?” reaction) this April. I called GoDaddy support April 18 but got no insight. The rep raised the question of whether it might be a hack to my browser rather than the site. Two kind commenters told me they’d seen it – Brad on May 3 and Andrew on May 13. Thanks, guys! So I’m not crazy, and it’s not just my browser.
I first saw it very briefly (and then not there – triggering the usual “Did I really see that!?” reaction) this April. I called GoDaddy support April 18 but got no insight. The rep raised the question of whether it might be a hack to my browser rather than the site. Two kind commenters told me they’d seen it – Brad on May 3 and Andrew on May 13. Thanks, guys! So I’m not crazy, and it’s not just my browser.
Ssh’d into the root of my hosting account, I tried a find . -exec grep “handjob santa” {} \; -print , hoping to discover how the hack had been embedded. Unfortunately, GoDaddy has a robot that kills processes that run for more than a minute or so, so that command didn’t complete. I tried several variations of that find, including just running from the wordpress directory, but still got no joy. Of course there are lots of ways to obfuscate a text string, so that was hardly a definitive exploration.
While googling for evidence of other sites with a similar hack, I found none, but was startled to see several hits on my own pages. Of course following the links showed the current pages – with no hacked string. But bless Google’s digital heart, the green link with the URL just below the main line in each hit has a pulldown which includes a link to a cached copy of the page. Sure enough, those cached copies contain the hacked in link! Now I had several nice static instances to examine.
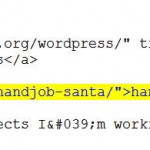 Looking at the page sources, the added links on both the “Jim’s Projects” and “Workshop 88” instances were immediately before a “</div>” tag: one at the end of the “site-title” div and the other at the end of the “site-description” div. That might be helpful.
Looking at the page sources, the added links on both the “Jim’s Projects” and “Workshop 88” instances were immediately before a “</div>” tag: one at the end of the “site-title” div and the other at the end of the “site-description” div. That might be helpful.
Armed with that, I called GoDaddy support again today (5/16/15), and Justin provided some valuable help. He pointed out that it might be related to the WordPress “theme” I was using. That makes sense. If you wanted your hack link to show up well, the site title and description sound like good places to put it.
But even better, he had me check my WordPress dashboard to see if there was an update to my theme. Such an update probably just overwrites the whole wp-content/themes/<this_theme> directory, and so might wipe out anything hidden in there. There was an update, I installed it, and it might have fixed the problem! Unlike my experience, Justin consistently saw the hack link on live pages of my site. After the update, they were gone!
I made a script to get the filenames and sums of all the .php files under wordpress, and ran it to get a snapshot. I think that will let me spot any changed .php files if it happens again. I also tarred and gzipped a copy of the themes directory in case they do the same thing again before there’s a new themes version to conveniently overwrite the bad stuff with.
What a nuisance!

It sounds like someone adds the link, then deletes it later. If so, you need a cron job verifying your checksums every 10 minutes or so.
If the link is dead as you found, maybe it’s from a Windows machine somewhere that was hacked years ago and never patched. A zombie PC.
The “hack” appears to be resolved! Great work! Before, I saw the link on all “detailed view” pages on multiple occasions (actually, all occasions). For that reason, I tend to agree that your theme files must have been tampered with.
Thanks for the update and confirmation, Andrew. I’ve been watching, and I also haven’t seen it since I replaced the ‘theme’ directory.
So bizarre! Unless they used a unique string for each account infected, I can’t imagine why Google didn’t find any other hits on ‘handjob santa’. And if they were just targeting my site – why?? And why so benign? My whole hosting account got hacked a couple of years ago (apparently by some Pakistani hackers) and their messages were umm, not benign. Took a lot of work to clean that up (with all its back doors), but at least my anger left me with a memorable password root 🙂
I also chased opengadgets.net and it looked like it was probably for a legit but folded enterprise. I considered contacting the domain admin from whois info, but didn’t.
Anyway, seems to be clean now. Thanks for watching!
Jim